11. Clean Resources
Overview
This section provides comprehensive instructions for cleaning up all AWS resources created during the Identity Governance workshop to avoid unnecessary charges.
Important Notes
⚠️ Warning: Following these cleanup steps will permanently delete all resources and data created during the workshop. Make sure you have backed up any important configurations or data before proceeding.
Cleanup Order
Resources should be cleaned up in the following order to avoid dependency conflicts:
- Lambda Functions and EventBridge Rules
- Step Functions State Machines
- DynamoDB Tables
- S3 Buckets and Objects
- CloudWatch Resources
- IAM Roles and Policies
- CloudFormation Stacks
- AWS Organizations (if created)
- IAM Identity Center (if no longer needed)
Step 1: Lambda Functions and EventBridge
Delete Lambda Functions
- Open AWS Lambda console
- Filter functions by workshop names:
- AccessCertificationTrigger
- PrivilegeAnalyticsEngine
- RiskAssessmentEngine
- CustomMetricsPublisher
- DailyOperationsEngine
- AuditReportGenerator
- E2EValidationTest
- Select each function
- Click Actions → Delete
- Confirm deletion by typing confirm
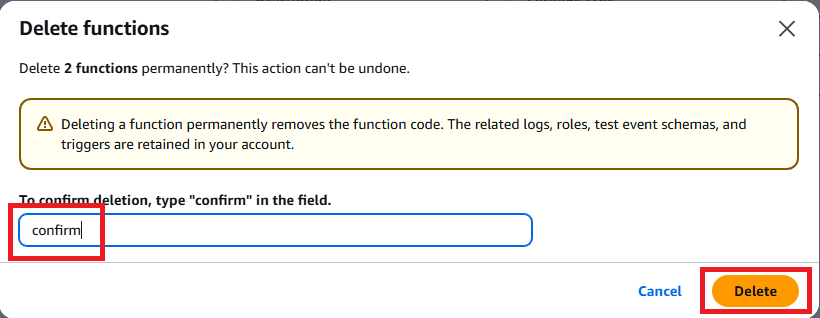
Delete EventBridge Rules
- Open Amazon EventBridge console
- Go to Schedules
- Select workshop rules:
- AccessCertificationSchedule
- ComplianceValidationSchedule
- RiskAssessmentSchedule
- DailyOperationsSchedule
- WeeklyOperationsReview
- Click Delete for each rule
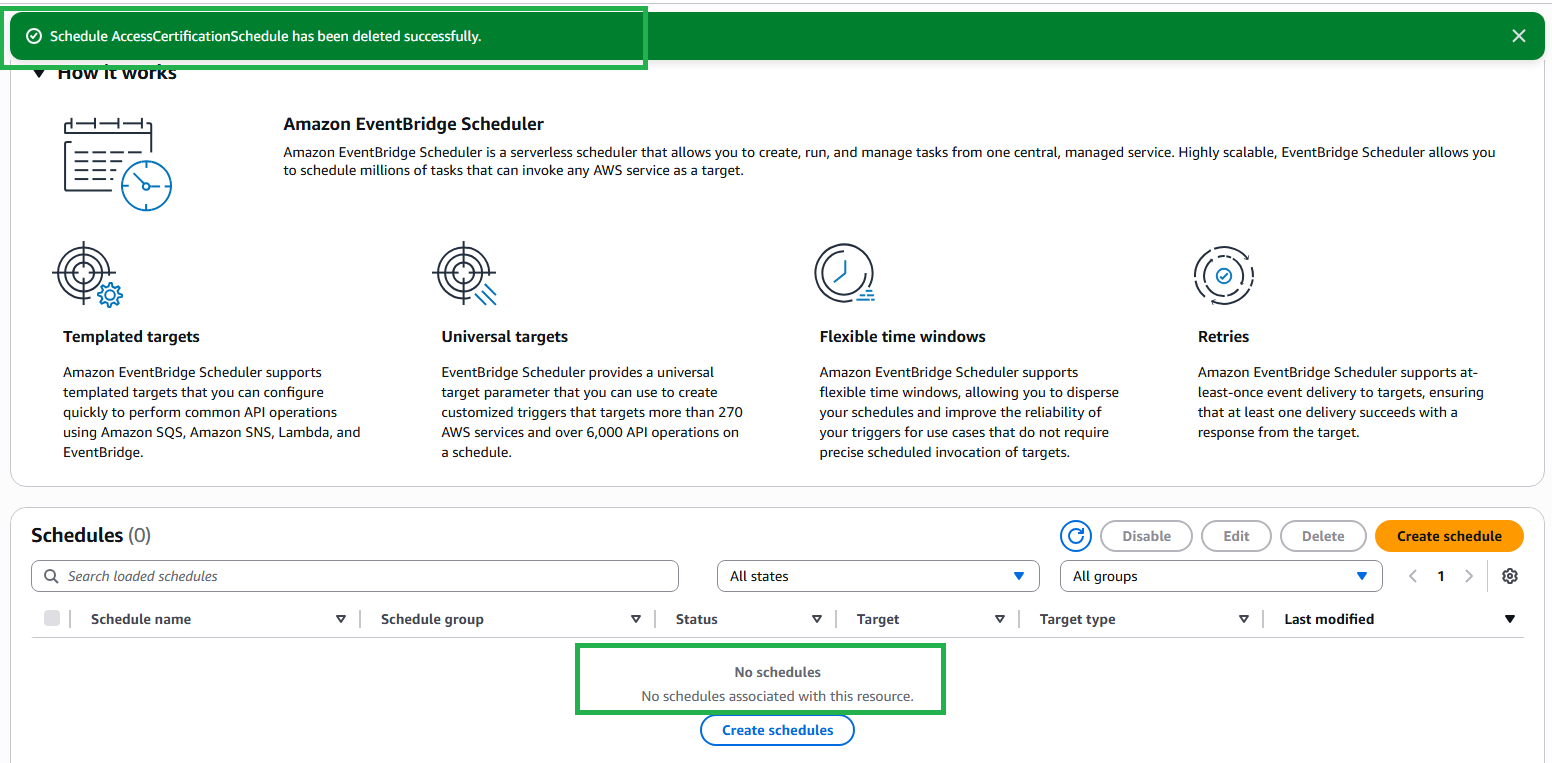
Step 2: DynamoDB Tables
- Open Amazon DynamoDB console
- Go to Tables
- Select workshop tables:
- AccessCertifications
- RiskAssessments
- CertificationTasks
- OperationsLog
- ComplianceEvidence
- RiskMonitoring
- AuditFindings
- Click Delete for each table
- Type delete to confirm
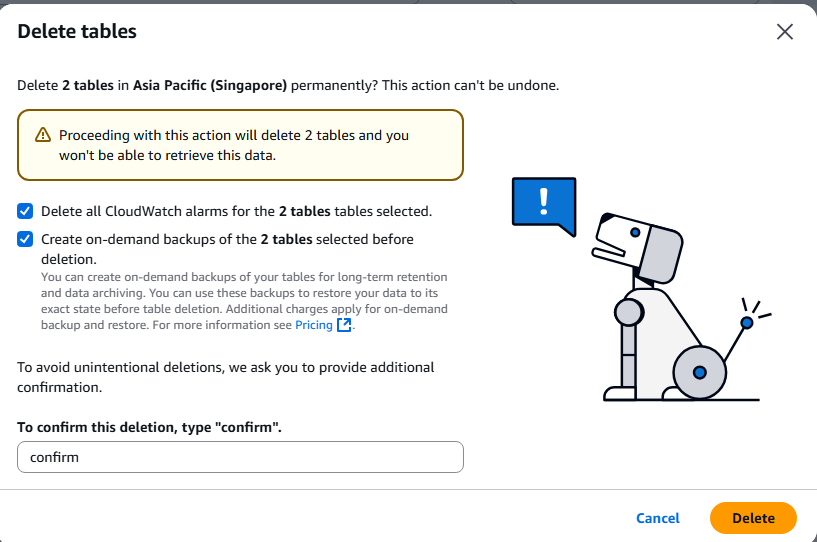
Step 3: S3 Buckets
Empty S3 Buckets
- Open Amazon S3 console
- Identify workshop buckets:
- identity-governance-analytics
- identity-governance-reports
- aws-cloudtrail-logs-* (CloudTrail bucket)
- Select each bucket and click Empty
- Type
permanently deleteto confirm
Delete S3 Buckets
- After emptying, select each bucket
- Click Delete
- Type bucket name to confirm
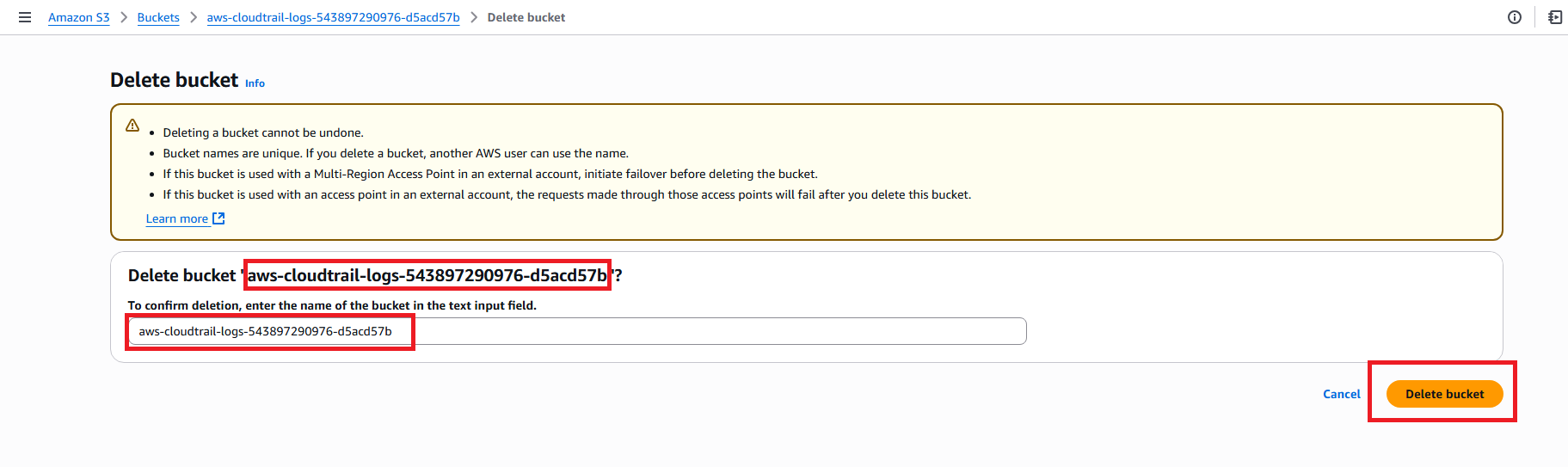
Step 4: CloudWatch Resources
Delete CloudWatch Dashboards
- Open Amazon CloudWatch console
- Go to Dashboards
- Select workshop dashboards:
- IdentityGovernanceRiskDashboard
- IdentityGovernanceOperations
- DailyOperationsDashboard
- Click Delete for each dashboard
Delete CloudWatch Alarms
- Go to Alarms
- Select workshop alarms:
- Lambda-AccessCertification-Errors
- HighRiskUserCount-Alarm
- DynamoDB-ReadErrors
- S3-AccessErrors
- Click Actions → Delete
Delete Log Groups
- Go to Log groups
- Select workshop log groups:
/aws/lambda/AccessCertificationTrigger/aws/lambda/PrivilegeAnalyticsEngine/aws/lambda/RiskAssessmentEngine/aws/lambda/CustomMetricsPublisher/aws/lambda/DailyOperationsEngine/aws/lambda/AuditReportGenerator/aws/lambda/E2EValidationTest
- Click Actions → Delete log group
Step 5: SNS Topics
Open Amazon SNS console
Go to Topics
Select workshop topics:
- IdentityGovernanceAlerts
- ComplianceAlerts
- RiskAssessmentAlerts
- DailyOperationsAlerts
Click Delete for each topic
Confirm deletion
Step 6: IAM Resources
Delete IAM Roles
- Navigate to IAM service in AWS Console
- Click Roles in the sidebar
- Search for workshop roles:
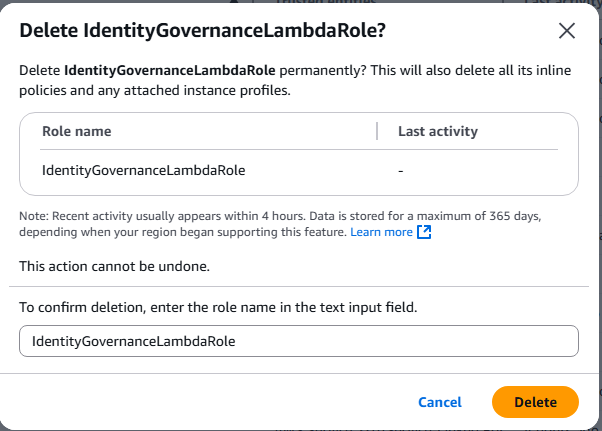
- IdentityGovernanceLambdaRole
- ComplianceValidationRole
- CertificationWorkflowRole
- Select each role and click Delete
- Type role name to confirm deletion
Delete Custom IAM Policies
Click Policies in the sidebar
Filter by Customer managed
Search for workshop policies:
- SecurityAuditPolicy
- IdentityGovernancePolicy
- ComplianceValidationPolicy
Select each policy and click Actions → Delete
Confirm deletion
Delete IAM Users and Groups
- Click Users in the sidebar
- Select workshop users and click Delete
- Click User groups in the sidebar
- Select workshop groups and click Delete
Step 7: Clean up IAM Identity Center
Delete Permission Set Assignments
- Navigate to IAM Identity Center
- Click AWS accounts in the sidebar
- Select your account and click Remove access
Delete Permission Sets
- Click Permission sets in the sidebar
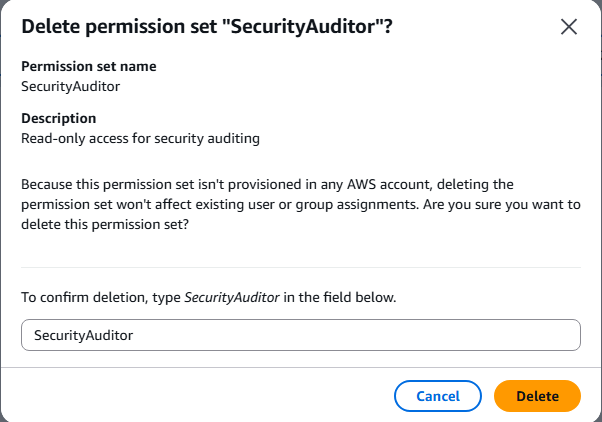
- Select workshop permission sets:
- SecurityAuditor
- ComplianceReviewer
- Click Delete
Delete Users and Groups
Click Users in the sidebar
Select workshop users and click Delete
Click Groups in the sidebar
Select workshop groups and click Delete
Step 8: Clean up CloudTrail
- Navigate to CloudTrail service
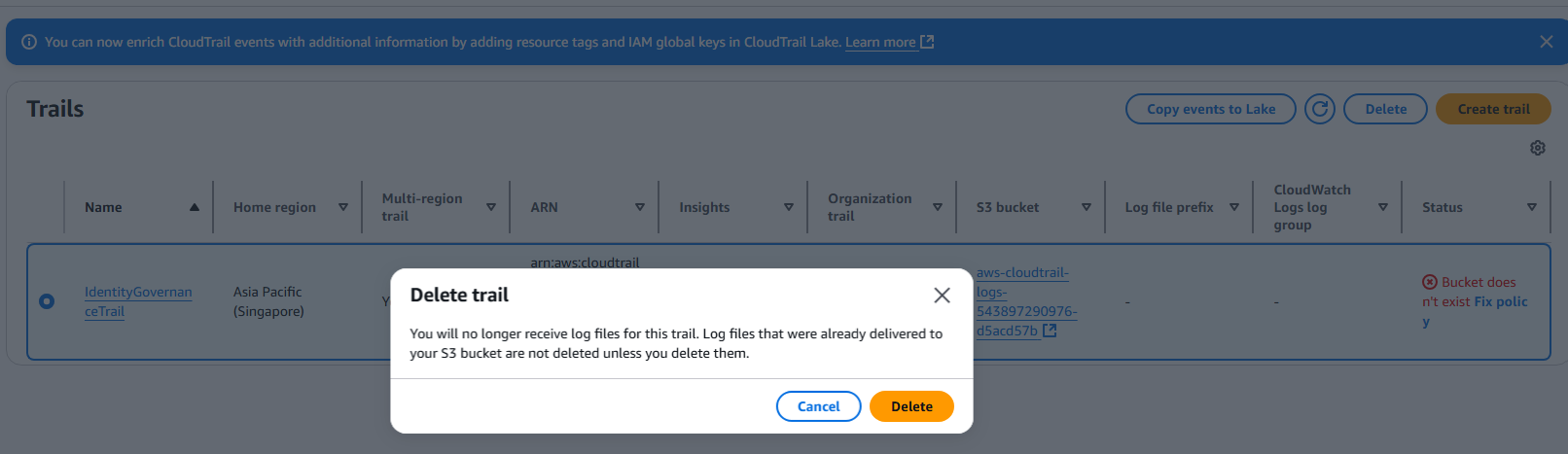
- Click Trails in the sidebar
- Select IdentityGovernanceTrail
- Click Delete
Console-Based Cleanup Checklist
For systematic cleanup through AWS Console, follow this checklist:
✅ Cleanup Checklist
Lambda Functions:
- AccessCertificationTrigger
- PrivilegeAnalyticsEngine
- RiskAssessmentEngine
- CustomMetricsPublisher
- DailyOperationsEngine
- AuditReportGenerator
- E2EValidationTest
EventBridge Rules:
- AccessCertificationSchedule
- ComplianceValidationSchedule
- RiskAssessmentSchedule
- DailyOperationsSchedule
- WeeklyOperationsReview
DynamoDB Tables:
- AccessCertifications
- RiskAssessments
- CertificationTasks
- OperationsLog
- ComplianceEvidence
- RiskMonitoring
- AuditFindings
S3 Buckets:
- identity-governance-analytics
- identity-governance-reports
- aws-cloudtrail-logs-[ACCOUNT-ID]-[HASH]
CloudWatch Resources:
- IdentityGovernanceRiskDashboard
- IdentityGovernanceOperations
- DailyOperationsDashboard
- All workshop alarms
- All workshop log groups
SNS Topics:
- IdentityGovernanceAlerts
- ComplianceAlerts
- RiskAssessmentAlerts
- DailyOperationsAlerts
IAM Resources:
- Workshop IAM roles
- Workshop custom policies (if any)
Optional Resources:
- AWS Security Hub (if not needed)
- AWS CloudTrail (if not needed)
Step 9: Cleanup Verification
Check Remaining Resources
- Check AWS Cost Explorer to confirm no charges are ongoing
- Use AWS Resource Groups to find tagged resources
- Search for tag: Project=IdentityGovernance
Check Final Services
- AWS Config: Disable configuration recorder if not needed
- AWS Security Hub: Disable if not used elsewhere
- Amazon GuardDuty: Disable if not needed
- AWS Audit Manager: Disable data collection
Workshop Cleanup Completed
Workshop cleanup completed successfully! 🎉